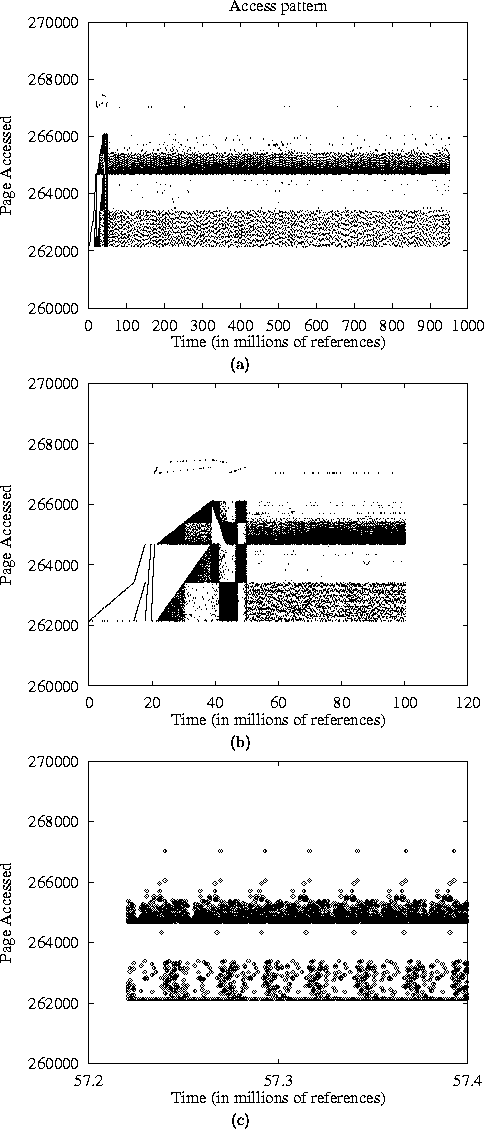
Figure 13: Access Patterns of N-BODY Simulation at three different zooming levels. We see that although the figure (a) suggests that there is little locality in the application, the rest two figures reveal surprisingly regular access patterns.
In this note we visualize the working set of several different applications, that are representative of various domains including numerical computations, databases, program development, and CAD simulation. We observe that most of the studied applications have regular and sometimes periodic access patterns. Even though some applications appear to have no regular access patterns at all, careful observation at the appropriate granularity reveal an impressively regular access pattern.

Figure 13: Access Patterns of N-BODY Simulation at three different
zooming levels. We see that although the figure (a) suggests that
there is little locality in the application, the rest two figures reveal
surprisingly regular access patterns.
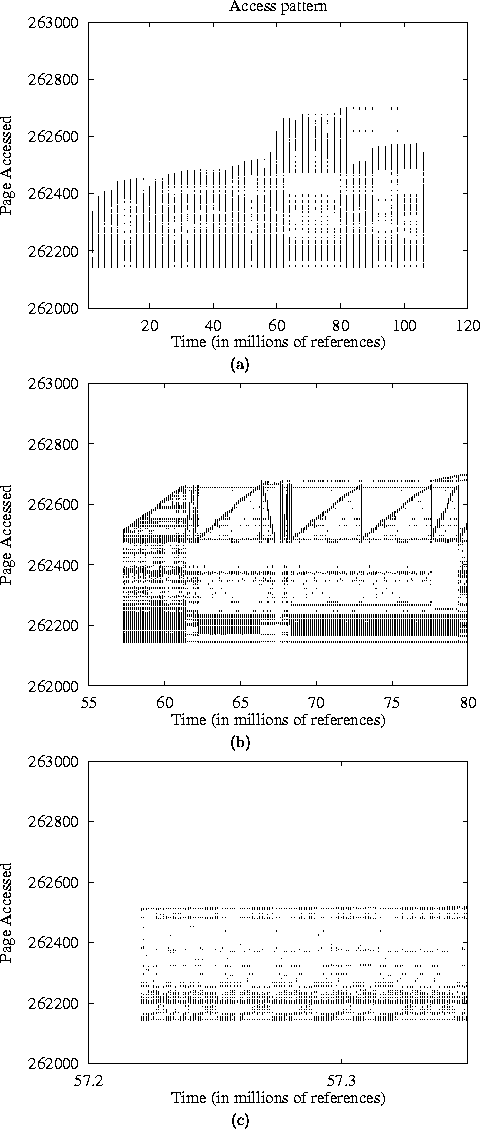
Figure 14: Access Patterns of GCC at three different
zooming levels. We see that although the fig. (a) suggests
little regularity in the access patterns of GCC, fig.
(b) shows long sequential accesses which can be seen only at
the appropriate zooming level.
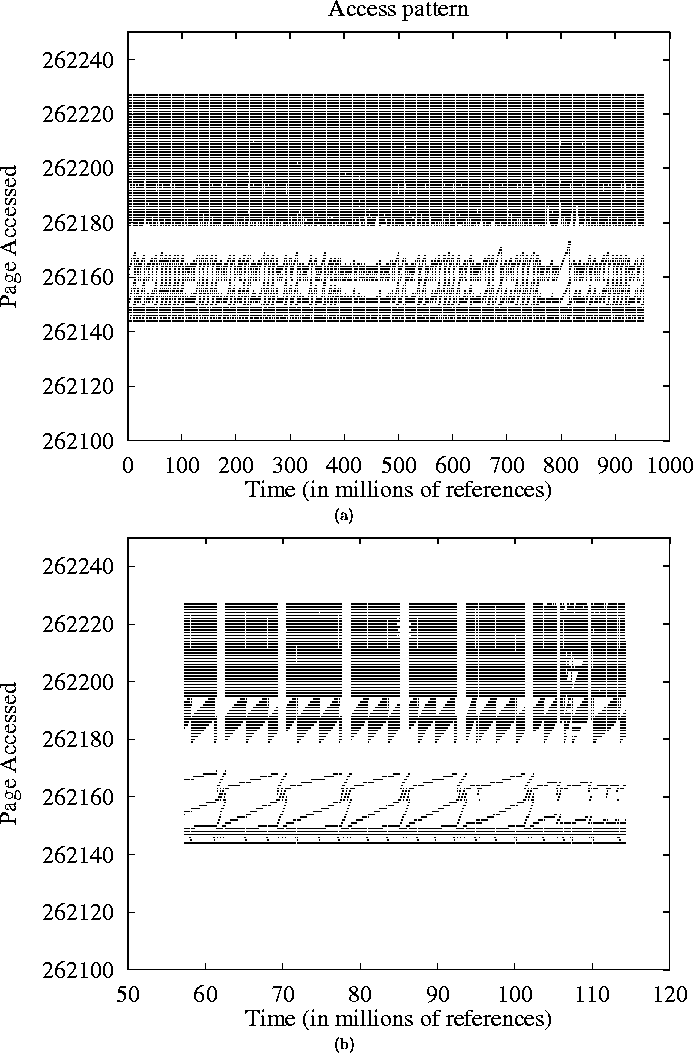
Figure 15: Access Patterns of GZIP at two different
zooming levels. We see that although the fig. (a) suggest that
there is little regularity in the application, fig. (b) reveals
surprisingly regular access patterns.
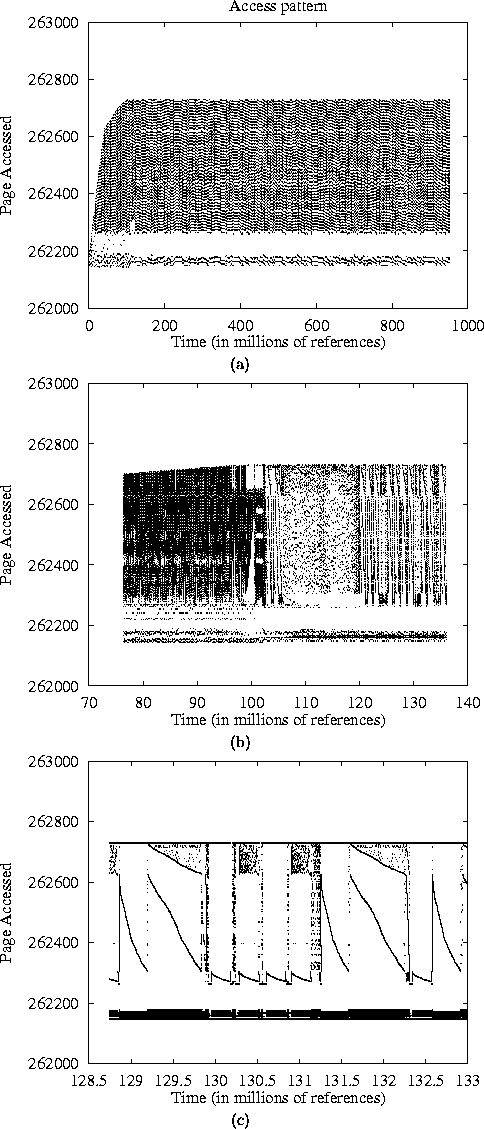
Figure 16: Access Patterns of ESIM at three different
zooming levels. Figures (b) and (c) reveal regular and sequential
access patterns.
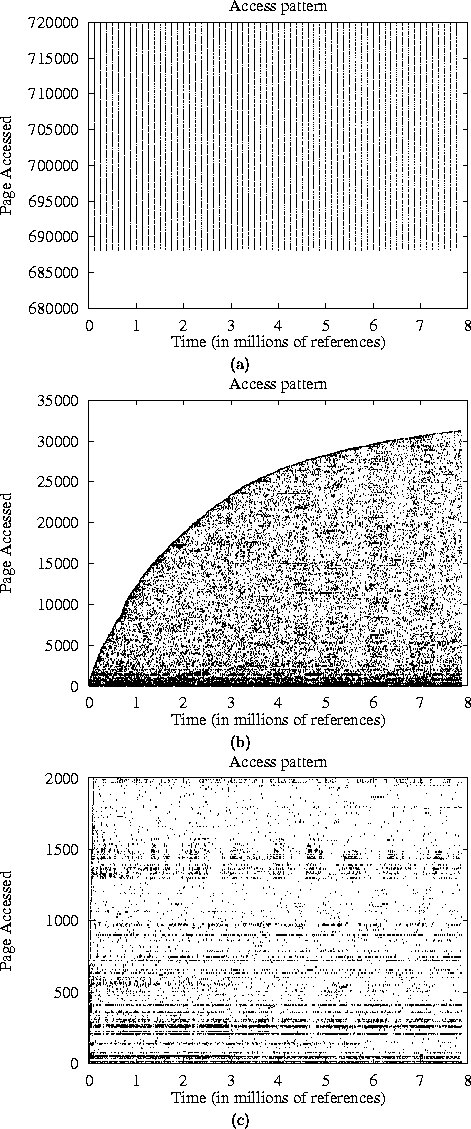
Figure 17: Access Patterns of SQL at three different
zooming levels. Figure (a) plots the virtual page accesses of the application.
To reveal any hidden regular access patterns that may reside in SQL, we
renamed the page numbers as follows: the first page to be accessed was assigned
number 0, then second page to be accessed was assigned number 1, etc.
Figures (b) and (c) show the (re-numbered) page accesses of the application.
Figure (c) shows a significant amount of locality, and some repeatability
in accessing some page clusters.