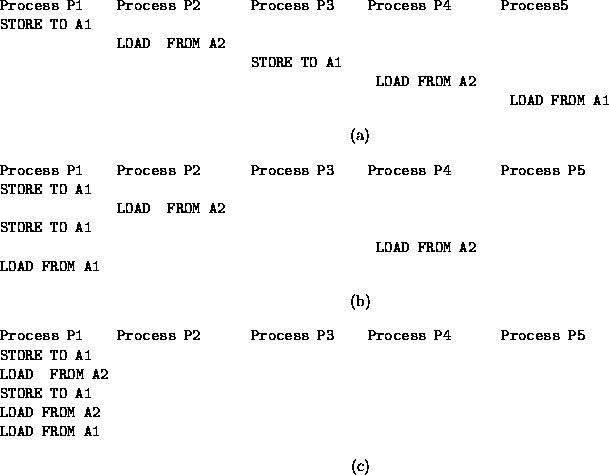
In this section we will (intuitively) show that the ``Repeated Passing of Arguments'' method initiates a DMA operation correctly. A DMA operation would be initiated incorrectly, only if the user-level processes that attempt to start a DMA are interrupted and interleave their arguments. Suppose that process P1 wants to start a DMA operation from memory location A1 to memory location A2. Suppose also that several other processes interleave their instructions with P1's. Although malicious processes may have read-only access to (possibly public) data A1, they do not have any access to private data A2. Assume, in the worst case, that all five instructions are issued by different processes as shown in figure 8(a). This interleaving implies that processes P1, P3, and P5 at about the same time want to make DMA operations with the same destination (source). That is different processes want at the same time to write to (or read from) the same physical address. If processes P1, P3, and P5 belong to different applications, then they should not be able to write-share the same physical memory location, since different applications do not write-share physical memory - thus, such an interleaving can't happen. If P1, P3, and P5 belong to the same application, then there should be some synchronization operation before they all attempt to write(read) the same memory location. We assume that applications that want to use user-level DMA are well written, which implies that there is a synchronization operation between any conflicting accesses to the same memory location by different processes of the same application. This synchronization operation should serialize DMA transfers. Thus, in any successfully started user-level DMA, instructions 1:, 3:, and 5: must come from the same process, resulting in the interleaving shown in figure 8(b).
If all accesses to A1 were issued by process P1, that process has also issued two intervening LOAD instructions to address A2, as well. Thus, if all accesses to address A1 have reached the DMA engine, the accesses to address A2 issued by process P1, must have reached the DMA as well. Thus, if a DMA is started all five instructions must have been issued by the same process (see figure 8(c)).
Thus, in any successfully started DMA, all instructions come from the same process, and there is no way for a malicious user to tamper with the mechanism of starting a DMA.
Figure 8: Possible interleaving of instructions in the Repeated passing
of argument DMA approach.