Security is a central concern in Communication Networks.
Secure communication requires a robust underlying network architecture.
A key characteristic of robust networks
is their ability to isolate, when required,
one flow (or aggregate of flows) from another,
so as to provide guaranteed QoS (quality of service)
to specific flows
in the presence of other, misbehaving flows
that share the same network links and resources.
This requires "multi-lane" architectures,
which eliminate head-of-line blocking.

Head-of-Line (HOL) Blocking:
Packets in communication networks are like cars in street networks. Shared queues and resources in network architectures are like single-lane streets: as shown on the right, congestion in one part of the network (blue cars) spreads out and affects all cars, including the green ones that are headed to uncongested directions. This phenomenon is known as Head-of-Line (HOL) Blocking.Network Vulnerabilities due to shared-queue (HOL blocking) architectures include:
- Lack of QoS guarantees;
- Lack of flow isolation;
- Congestion spread-out;
- Prone to DoS attacks.
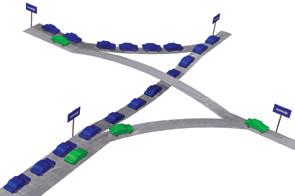
Multi-Lane Network Architectures:
As in highways, Multi-Lane Network Architectures are needed to eliminate the above vulnerabilities. In the figure on the right, green cars can use the second lane to overtake the congested blue cars and move quickly to their own, uncongested direction; emergency lanes for use by fire trucks, ambulance, and police cars work in the same way. In communication networks, the equivalent effect is achieved using Virtualization of the resources, based on Per-Flow Queues (or per-flow-aggregate queues) in order to isolate the flows from each other, plus appropriate, advanced Scheduling Algorithms in order to select the flows that should be serviced first so as to guarantee the desired quality of service for each flow.For robust and scalable multi-lane networks, the following research topics must be addressed:
- Architectures that are scalable to thousands of queues;
- Advanced scheduling algorithms and circuits for thousands of flows;
- Hierarchical flow aggregation,
to cope with the millions of microflows in the Internet.

Multi-Lane Network R&D at ICS-FORTH:
ATLAS I Chip (1996-98) - Switch Node for Robust Networks: This 6 million transistor single-chip ATM switch, that we designed in the mid-90's and was implemented in 0.35-micron CMOS, offered 10 Gigabits per second of aggregate throughput, while supporting 32 thousand Lanes. Managing so many lanes in a constrained technology was made possible by only keeping state information for the non-empty queues, using content-addressable memory (CAM).Per-Flow Queueing (1996-2001) - Managing Thousands of Queues at High Speed: Per-flow queueing typically requires the implementation of a large number of logical queues --hundreds or thousands to possibly millions in the future-- inside one or a few physical memories. When the communication system is to operate at high speed, the management of these multiple queues typically requires the assistance of specialized hardware. We have worked on such multi-queue management implementations at different cost and performance levels.
Weighted-Round-Robin (WRR) Scheduling (1985-2002): Our work started in 1985 with an investigation of several techniques for performing round-robin scheduling at high speed among a large number of flows. Later, in 1990, we designed a WRR scheduler for hundreds of flows, using a CAM in CMOS VLSI. More recently, since 1996, we developed techniques for WRR scheduling and Weighted Fair Queueing (WFQ) among many thousands of flows at a relatively low cost, or at very high speed.
Multiple Priority Levels in Buffered Crossbars (2003-04):
We proposed the effective use of two-lane limited resources
within a buffered crossbar switch,
by adaptively mapping onto them
the multiple priority levels supported by the line cards.
This two-level flow-aggregation scheme
performs almost identically to a multi-lane system,
by exploiting the relatively short round-trip time (RTT)
between its levels of hierarchy (line cards, crossbar switch)
and the consequent small size of the crossbar buffers.
| Up to
Information Security R&D
at ICS-FORTH Home Page |
© copyright ICS-FORTH 2004.
last updated: Sep. 2004, by M. Katevenis. |